Here’s a simple example how you may block the .zip top level domain with a webfilter profile on a FortiGate
You may use add a new URL Filter block in your webfilter profile
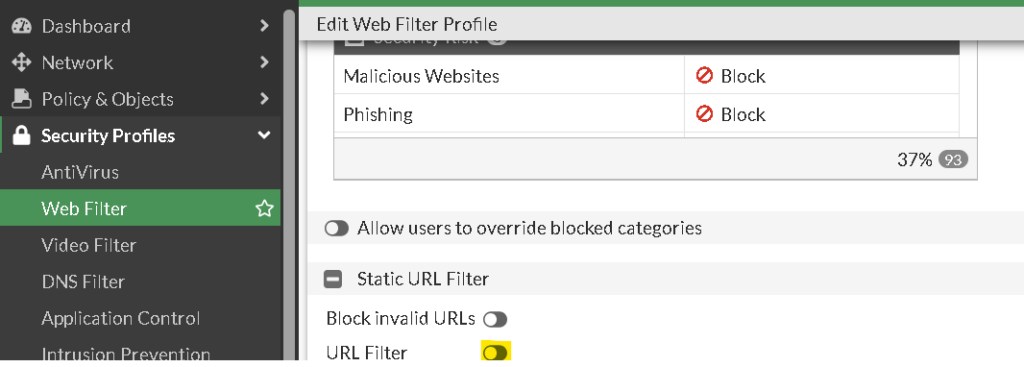
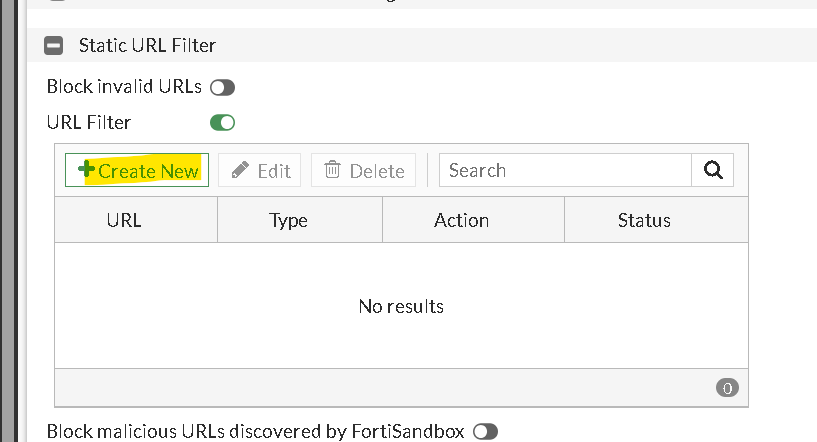
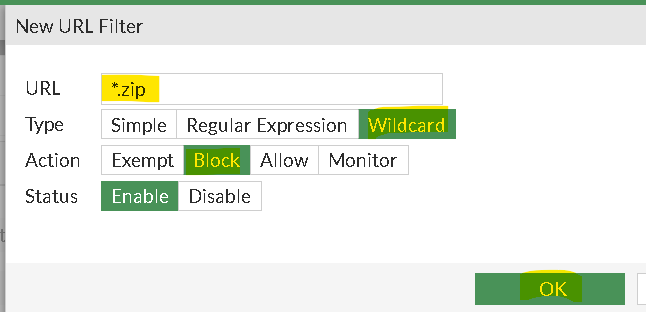
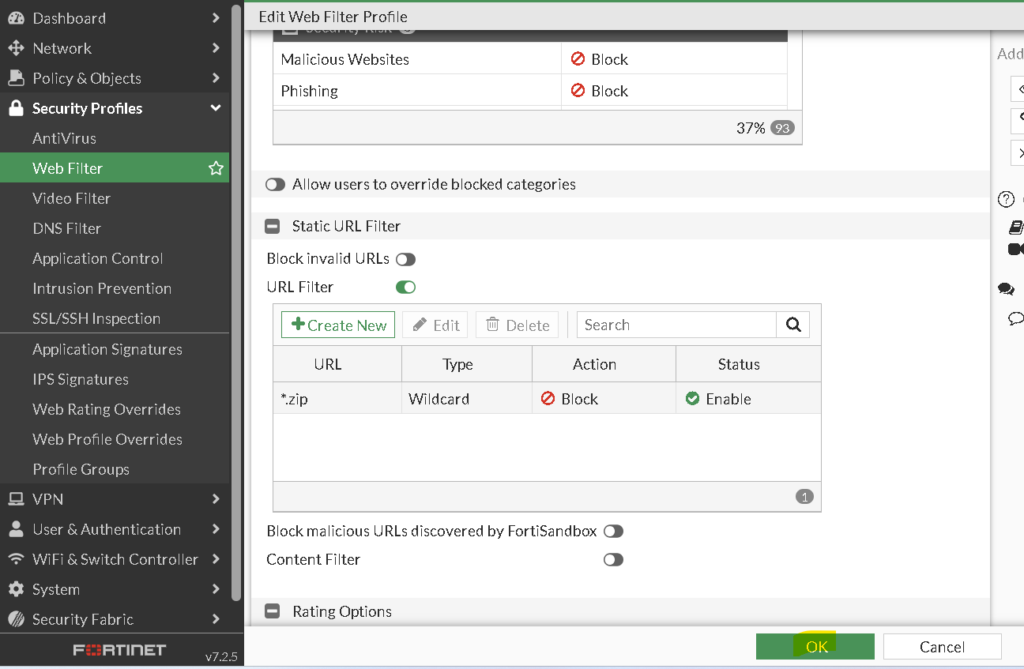
Now you’ve created a new URL Filter table, you may add it to your other Webfilter Profiles:
Please verify the ID of your newly created urlfilter-table, in my case i’ve added the URL Filter to the Webfilter with the name “WF_Guest”
show webfilter profile WF_Guest
config webfilter profile
edit “WF_GUEST”
set comment “Block only Malicious Websites”
config web
set urlfilter-table 3 # <– this is the id of your urlfilter-table
end
end
then choose the next webfilter you would like to add your URL Filter and configure the existing urlfilter-table id
config webfilter profile
edit “WF_Client”
set comment “Block only bad Websites”
config web
set urlfilter-table 3 # <– this is the id of your urlfilter-table
end
end
In the Gui you’ll see the same URL Filter on your other webfilter profiles.
If you perform a change, it will be applied on all webfilter profiles which are using your newly created urlfilter-table.
After this change the policies which are using the Webfilter and certificate inspection web access to .zip Domains will be blocked.
